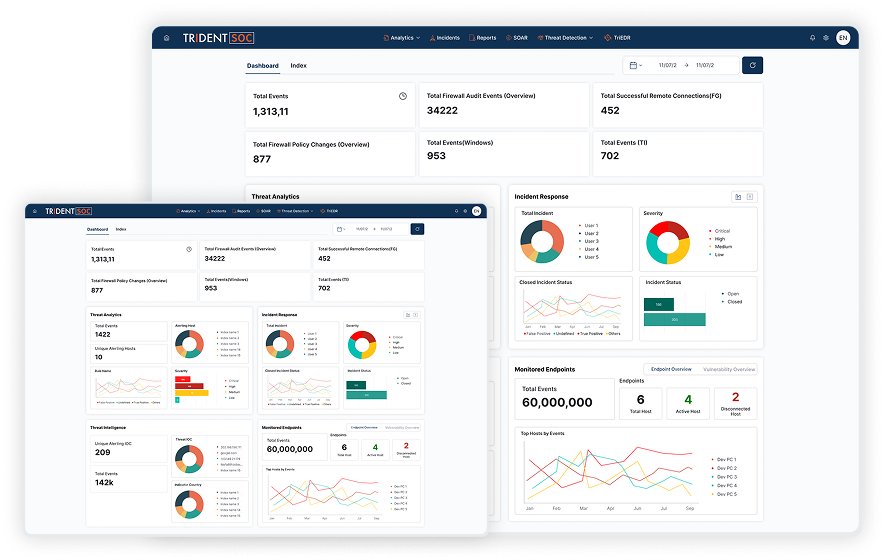
Key Features
Unified, proactive, and automated protection for your digital ecosystem, designed to safeguard your business with proactive threat detection, comprehensive visibility, and a reliable cybersecurity solution tailored to your needs.
Expert-Led 24/7 Operations
A certified team of security analysts monitors, investigates, and responds to incidents in real time, providing both the technology and the people to ensure your organisation is always protected.
UEBA & SOAR Automation
Our platform uses User Entity and Behavior Analytics to monitor how users and systems behave to spot anything unusual, while Security Orchestration Automation and Response automatically investigates and fixes issues without delay.
Advanced Threat Detection
Leverages over 5,000 detection rules and machine learning algorithms to identify known and unknown threats across endpoints, networks, cloud, and applications.
Traditional Security Is Not Enough Anymore
Over 90% of successful cyberattacks exploit gaps missed by traditional monitoring. Modern threats demand real-time visibility, automation, and expert-led response.
Decision Factor
Trident SOC Platform
Built on Trident, providing a modern, unified system designed to correlate data across the entire environment.
Uses Machine Learning analytics, including UEBA and threat intelligence feeds, to proactively hunt for threats.
Our SOAR-powered playbooks can automatically contain threats, and our certified experts manage complex responses quickly.
We handle all platform management, including updates, scaling, maintenance, and rule optimisation.
Our automated report engine generates audit-ready compliance reports, saving your team time and effort.
One subscription covers the platform and expert service, with no hidden costs for software or hardware.
Traditional MDR Services
Built on your existing security tools.
These services primarily review the alerts generated by the tools.
When a threat is detected, your team is responsible for executing the response.
You are responsible for managing your licenses, updates, scaling, and tuning.
You must manually gather and consolidate data from multiple tools to produce compliance-ready reports.
MDR fee plus underlying tool costs and administrative effort.
How Does Trident SOC Work?
Trident SOC operates as a fully managed 24/7 security operations centre, combining advanced technology with expert oversight to detect, respond to, and prevent cyber threats.
We Monitor Over Your Systems 24/7
Our advanced tool constantly monitors your entire digital environment, including cloud, network, endpoints, and applications.
We Detect Anything Suspicious Early
Using advanced analytics and threat intelligence, Trident identifies potential threats before they impact your business.
We Take Action Before Damage Happens
When a threat is detected, our automated playbooks and team quickly investigate, contain, and remediate incidents, reducing business impact.
We Prevent Future Attacks
Continuous vulnerability assessments, compliance reporting, and system hardening help prevent future incidents and reduce exposure to evolving threats.

Who is Trident SOC For?
Trident SOC provides enterprise-grade security to businesses across industries, helping them detect and build a robust cybersecurity network without the need to build an in-house SOC.
Tech Companies & SaaS Providers
Real-time protection across apps, networks, and cloud to reduce downtime and security risk.
Growing SMEs
24/7 SOC coverage delivering enterprise-grade security without added cost or complexity.
Financial Services
Proactive defense for financial data and payment systems while maintaining compliance.
Healthcare
Continuous protection for patient data and clinical systems against advanced threats.
Educational Institutions
Secure monitoring to protect student, staff, and research data across digital platforms.
IT & Cloud Service Providers
Unified monitoring and response to safeguard client environments with minimal overhead.
Government & Public Sector
Advanced protection for sensitive data and critical infrastructure with strict compliance.
Let’s Build a Security Plan That's Right For You
Connect with our experts to design a tailored plan that ensures your organisation stays secure, compliant, and resilient against evolving threats.